IT-Custodian
It is a constant challenge to securely make applications and data available to all authorised people, on any device, at any location and at all times while preventing access to unauthorised people and those with malicious intent. Recognising this critical need, IT-Custodian is a powerful combination of protection and support. It delivers resilience, offering state-of-the-art IT support and cybersecurity solutions designed to safeguard your enterprise against the myriad threats lurking in the digital shadows.
Managed IT Support & Security
| Core hours – Mon-Fri | Extended hours – Mon-Fri | 24×7 | |
|---|---|---|---|
| NOC & SOC monitoring | 24×7 | 24×7 | 24×7 |
| NOC & SOC fix | 9 to 5:30 | 8 to 8 | 24×7 |
| Service Desk | 9 to 5:30 | 8 to 8 | 24×7 |
| Remote server and network support | 9 to 5:30 | 8 to 8 | 24×7 |
| On-site support (if included) | 9 to 5:30 | 9 to 5:30 | 9 to 5:30 |
| Patches and updates | Included | Included | Included |
| Malware monitoring | Included | Included | Included |
| System changes, user adds, user modifications and other admin tasks under 15 minutes | Unlimited 9 to 5:30 | Unlimited 9 to 5:30 | Unlimited 9 to 5:30 |
| Warranties and software licence management | Included | Included | Included |
The Service Desk
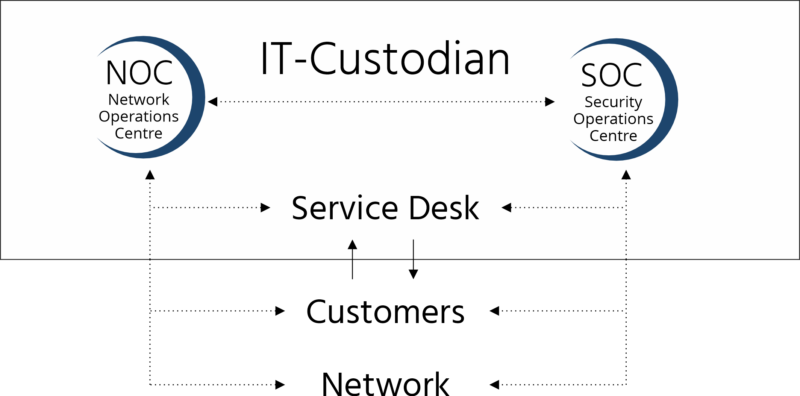
The Service Desk provides a single point of contact for our clients to log calls and cases. The Service Desk can assist with all services under management and supported infrastructure. The Service Desk staff will work with you to diagnose the issue and then allocate it to the most appropriate resource for resolution. The Service Desk provides for case logging and management of:
- Incidents
- Problems
- Remote Moves, Adds Changes (RMACs)
- Escalations
Once you’ve reported the incident, you know that the Service Desk will take care of everything; all case management activities including the coordination of manufacturers, escalation management and incident progression. We log every call and, to keep your network safe, only named users will be able to log a support call.
You can log a call by phone, email, the customer portal or through your device’s software agent.
Cybersecurity Checklist
IT-Custodian’s multi-layered approach is designed to provide maximum protection. The Cybersecurity Checklist helps you prove adherence to standards, compliance or with cybersecurity insurance. These services are available to you based on the level of service provision you have agreed to.
Incident Response and Detection
Content and Filtering Security
Endpoint Security
Network Security
* Available with IT-Custodian Plus